Stubby

OpenWrt can be configured to support encrypted DNS requests. The relevant software packages stubby and dnsmasq can be installed from the repositories.
All articles of the OpenWrt series
Packages
dnsmasq-full= It is intended to provide coupled DNS and DHCP service to a LAN.stubby= This package contains the Stubby daemon (which utilizes the getdns library).
stubby
opkg install stubby
Start stubby
/etc/init.d/stubby start
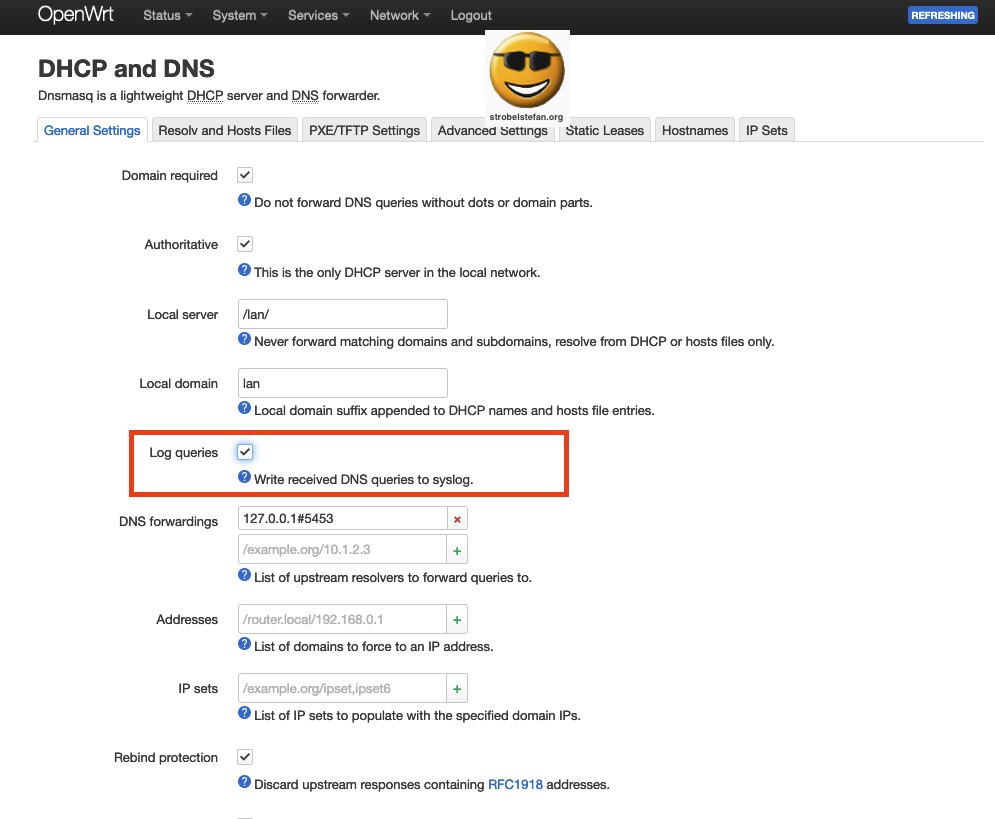
To use stubby as the DNS server you have to edit the config file /etc/config/dhcp
nano /etc/config/dhcp
Just add the two lines at the end of the config dnsmasq section.
config dnsmasq
...
option noresolv '1'
list server '127.0.0.1#5453'
Restart log, dnsmasq and stubby services via LuCi or on the CLI.
/etc/init.d/log restart; /etc/init.d/dnsmasq restart; /etc/init.d/stubby restart
dnsmasq
The package dnsmasq is part of the standard OpenWrt installation.
For this configuration dnsmasq-full is needed.
The command will
- download
dnsmasq-full - remove
dnsmasq - install
dnsmasq-full
During installation, modified config files are not overwritten, but the new config files are stored in /etc/config/dhcp-opkg.
opkg install dnsmasq-full --download-only && opkg remove dnsmasq && opkg install dnsmasq-full --cache . && rm *.ipk
During installation, modified config files are not overwritten, but the new config files are stored in /etc/config/dhcp-opkg.
Edit the config file /etc/config/dhcp again to make the necessary changes
nano /etc/config/dhcp
Add the two lines at the end of the config dnsmasq section.
config dnsmasq
...
option dnssec '1'
option dnsseccheckunsigned '1'
Restart log, dnsmasq and stubby services via LuCi or on the CLI.
/etc/init.d/log restart; /etc/init.d/dnsmasq restart; /etc/init.d/stubby restart
Do It The Nerdy Way 😄
The configuration we have done above with the editor nano can be done directly in CLI. Just execute the commands to add the lines to the respective files.
Edit /etc/config/dhcp
uci add_list dhcp.@dnsmasq[-1].server='127.0.0.1#5453'
uci set dhcp.@dnsmasq[-1].noresolv=1
uci commit && reload_config
Tell OpenWrt only to use our own DNS server (= custom DNS servers) and not DNS server provided by ISP.
Edit /etc/resolv.conf
uci set network.wan.peerdns='0'
uci set network.wan.dns='127.0.0.1'
uci set network.wan6.peerdns='0'
uci set network.wan6.dns='0::1'
uci commit && reload_config
DNSSEC Validation
uci set dhcp.@dnsmasq[-1].dnssec=1
uci set dhcp.@dnsmasq[-1].dnsseccheckunsigned=1
uci commit && reload_config
The result you can verify with cat.
cat /etc/config/dhcp
cat /etc/resolv.conf
Edit /etc/config/stubby
Add custom DNS servers
nano /etc/config/stubby
Add the lines at the end of the config file:
config resolver
option address '80.241.218.68'
option tls_auth_name 'fdns1.dismail.de'
list spki 'sha256/MMi3E2HZr5A5GL+badqe3tzEPCB00+OmApZqJakbqUU='
config resolver
option address '5.9.164.112'
option tls_auth_name 'dns3.digitalcourage.de'
list spki 'sha256/2WFzfO2/56HpeR+v/l25NPf5dacfxLrudH5yZbWCfdo='
All other config resolver sections can be commented or deleted from the file.
⚠️ Verify the DNS server information on the provider's site!!!
Add a Stubby parameter to the config stubby 'global' section in /etc/config/stubby.
config stubby 'global'
[..]
option tls_min_version '1.2'
Restart log, dnsmasq and stubby services via LuCi or on the CLI.
/etc/init.d/log restart; /etc/init.d/dnsmasq restart; /etc/init.d/stubby restart
Log Files
# All OpenWrt logs
logread
# Log filter for Stubby
logread -e stubby; netstat -l -n -p | grep -e stubby
# Log filter for DNSMASQ
logread -e dnsmasq; netstat -l -n -p | grep -e dnsmasq
Testing
To run the dig command on OpenWrt an additional package is required
opkg install bind-dig
Run a test. Replace the IP address against the IP address of your OpenWrt device.
dig dnssectest.sidn.nl +dnssec +multi @192.168.xxx.xxx
; <<>> DiG 9.18.7 <<>> dnssectest.sidn.nl +dnssec +multi @192.168.xxx.xxx
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 56660
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags: do; udp: 1232
;; QUESTION SECTION:
;dnssectest.sidn.nl. IN A
;; ANSWER SECTION:
dnssectest.sidn.nl. 3600 IN A 212.114.120.64
dnssectest.sidn.nl. 3600 IN RRSIG A 13 3 3600 (
20221205164950 20221120160928 39816 sidn.nl.
OlRU2tPQuzSAV5L/9tDhucqcIfAAwATznLQygE+1RzUN
eHf8iSrluLUTDvsd09veZ5sturiyMFGEFOYlEewRlQ== )
;; Query time: 440 msec
;; SERVER: 192.168.xxx.xxx#53(192.168.xxx.xxx) (UDP)
;; WHEN: Mon Nov 28 16:21:21 CET 2022
;; MSG SIZE rcvd: 166
The flag ad is important. It shows that the DNSSEC works.
...
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
...
Hijack DNS
Configure firewall to intercept DNS traffic in lan via LuCi.
The rule "changes" all DNS queries within lan and send it to the OpenWrt device on IP 192.168.200.1.
Firewall - Port Forwards - intercept-dns-in-lan
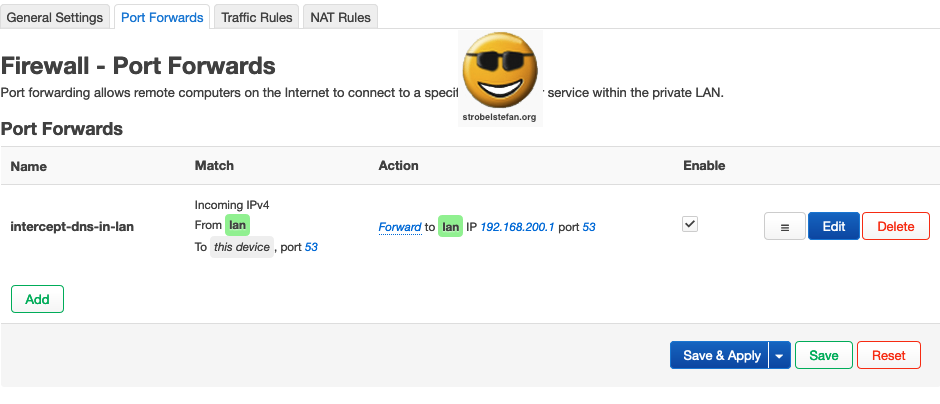
General Settings
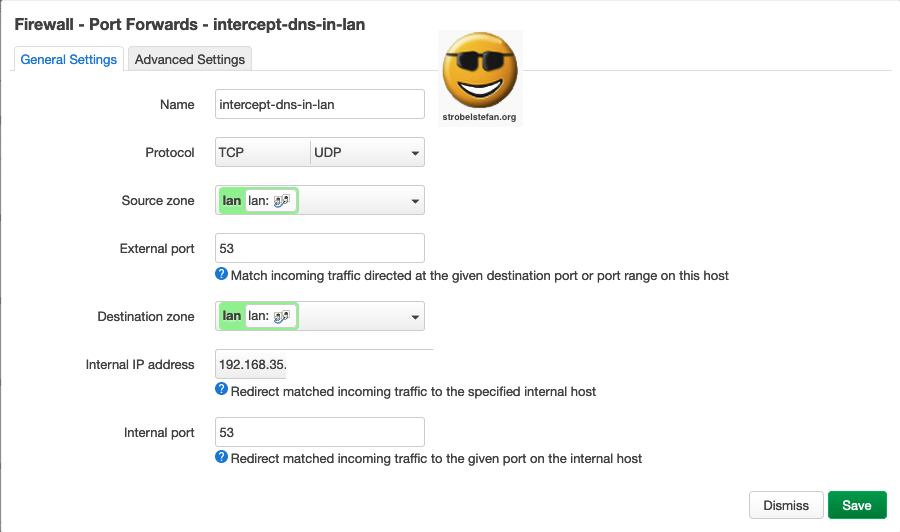
Advanced Settings
- 🔗 https://warlord0blog.wordpress.com/2022/02/13/OpenWrt-dns-hijacking/
- 🔗 https://OpenWrt.org/docs/guide-user/firewall/fw3_configurations/intercept_dns
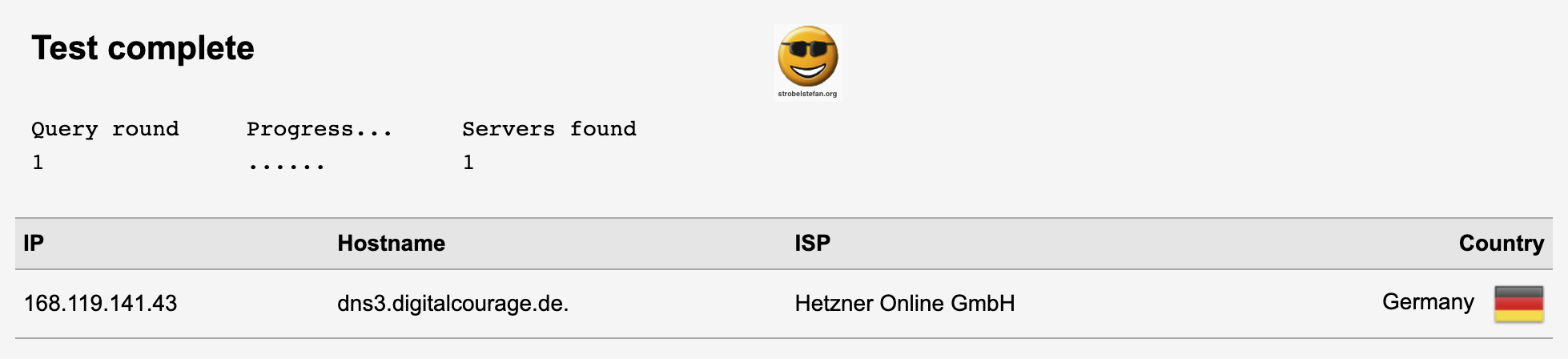
DNS Leakage Test
A DNS test can be performed on each client:
The test should show the configured OpenWrt's DNS server ➡️ Edit /etc/config/stubby.
Pi-hole
When you run a Pi-hole within your network to block adds then you can redirect the DNS queries to the OpenWrt's secure DNS server.
The Pi-hole reporting functions are much more user-friendly than the adblock. So it makes sense to run a Pi-hole if you would like to have a detailed reporting in a nice web format.
If you have Pi-hole with unbound your DNS will be
127.0.0.1#5335
````
{max-height=50% width=auto}
Pi-hole can still be embedded into the network can be used as a sinkhole for ads.
```text
<ip-address-of-OpenWrt>#53
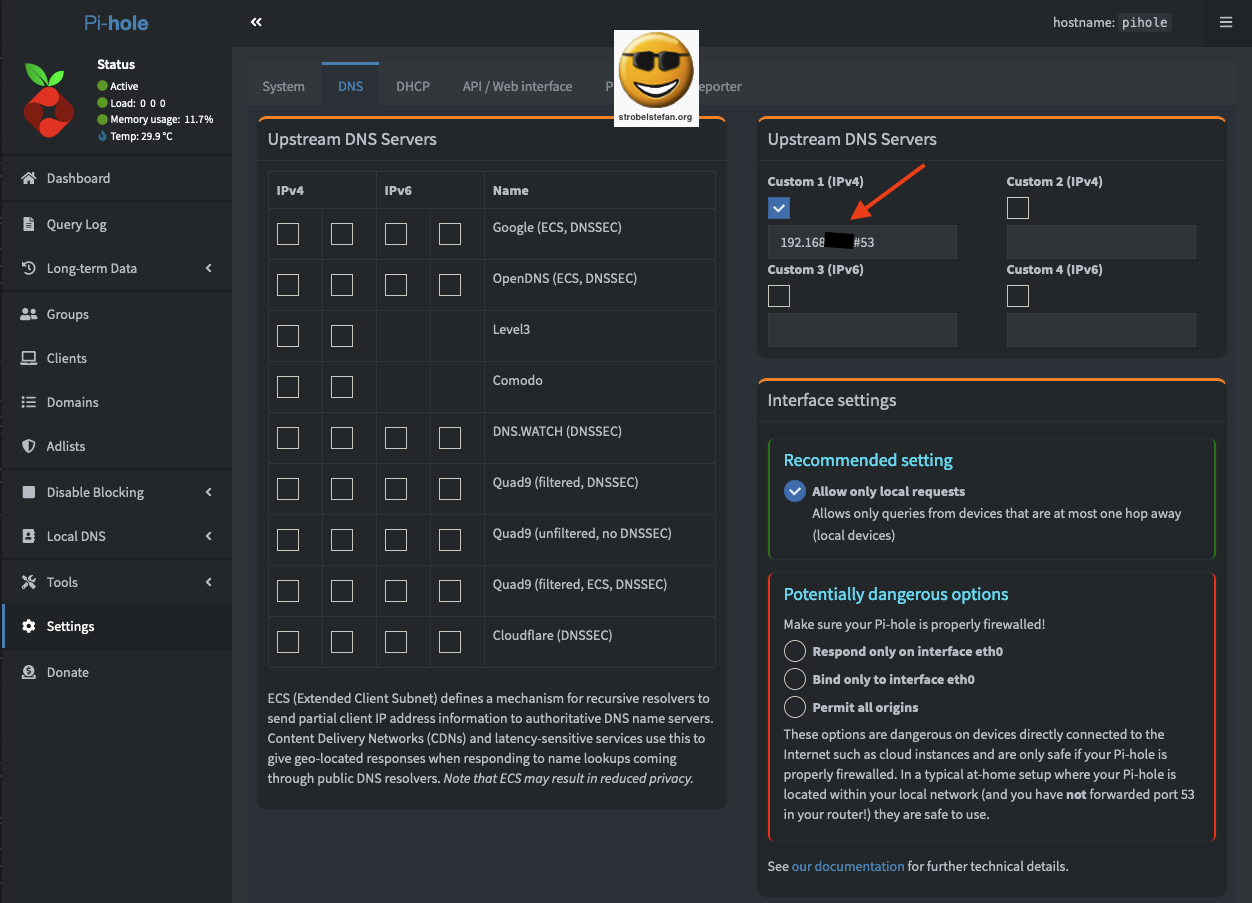
The query log on the Pi-hole shows the DNS server is the DNS server on the OpenWrt device.
All articles of the OpenWrt series
Gib mir gerne einen Kaffee ☕ aus ❗️
Wenn dir meine Beiträge gefallen und geholfen haben, dann kannst du mir gerne einen Kaffee ☕️ ausgeben.
Follow Me❗️
Source
Image: Official OpenWrt Logo - https://OpenWrt.org/_media/docs/guide-graphic-designer/OpenWrt-logo-usage-guidelines.pdf - 🔗 https://www.kuketz-blog.de/stubby-verschluesselte-dns-anfragen-OpenWrt-teil5/ - 🔗 https://candrews.integralblue.com/2018/08/dnssec-on-OpenWrt-18-06/ - 🔗 https://candrews.integralblue.com/2018/08/dns-over-tls-on-OpenWrt-18-06/



